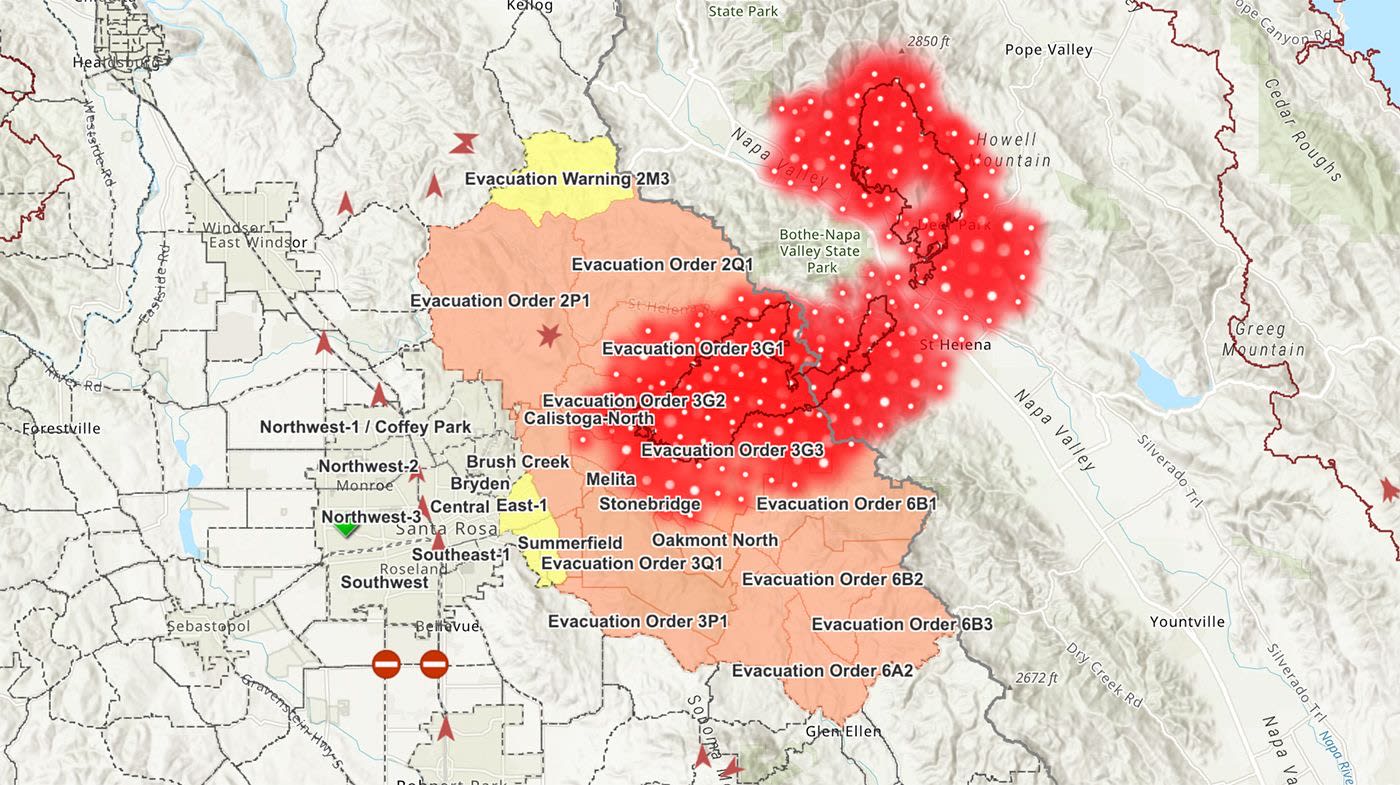
This solicitation is intended to present an overview of the transition of SCOUT to a new solution called NEXT-GEN SCOUT.
NEXT-GEN SCOUT shall provide a comprehensive, visual picture of the operating environment during an emergency incident. This tool must provide the following:
- A Common Operating Picture (COP) which allows for the contribution of data and analytics from and sharing of information with various public and private organizations.
- The ability to display multiple incidents simultaneously.
- Must operate in an all-hazard environment.
- Must provide a modern and easy-to-use user experience.
- Field workers with spotty/or no internet coverage must be able to use the application and have a synchronizing capability (store-and-forward) with no loss of data.
- Provide access controls for varied users: first responders, emergency managers, utilities, private and public organizations including government agencies such as, CAL FIRE, National Weather Service, FEMA, US Forest Service, Coast Guard, and Tribal.
REQUIREMENTS
In addition to detailed requirements for the NEXT-GEN SCOUT (attached), essential data requirements include:
GENERAL DATA
- Weather Data (NWS, GACC, etc)
- Live Video Feeds (Alert Wildfire Cameras, Traffic Camers)
- Transportation Data (Caltrans road closures)
- Census Data
- Critical Infrastructure
- Utilities
- Land Ownership
- Public Safety Facilities
- Airports
- Railroads
- Fire Station Locations and Apparatus
FIRE
- Wildland Fire Perimeter
- Direct Protection Areas
- Wildfire Topography
- Wildland Fuel Types
- Aircraft Flight Following
- Wildfire Modeling (WiFIRE)
- Urban Search & Rescue Symbology
LAW ENFORCEMENT
- Integration with Surveillance Cameras
- Automatic Vehicle Locators for Law Enforcement Vehicles
- Officer Tracking
- Evacuation Zones
- Evidence Collection
- Crime Scene Mapping and Documentation
- UAS Video Feed
EMERGENCY MEDICAL SERVICES
- Automatic Vehicle Locators for Ambulances
- Hospitals and Trauma Centers
- Hospital Emergency Room Status
- Mass Casualty Victim Mapping
- EMS Personnel Tracking
EMERGENCY MANAGEMENT
- Evacuation Zones
- Population Affected
- Resource Allocation
- Resource Availability
- Asset Management
- Incidents
- Damage Assessment
- County EOC Locations
- Live Video Feed
- Incident Checklists
- Critical Infrastructure
- Shelter Locations
- Alert and Warning Notifications
CONSTRAINTS
A cloud solution is preferred, and relevant Cal OES technologies include Microsoft 365, Azure AD, ESRI, Salesforce, Mulesoft, Tableau, Docusign, GovDelivery, SendGrid. MFA is being enabled and multiple SSO implementations have been deployed.
Information Security & Privacy Compliance Requirements
Minimum Security Requirements (NIST 800-53 Rev.4)
Access Control
- The application shall use account management and enforce access controls to ensure separation of duties to prevent abuse of authorized privileges.
- Concurrent Session Control.
- Session Lock/Termination Period should be established.
- Information Flow Enforcement. (Data Loss Prevention)
Auditing
- Ensure that security events are audited and protected to include unsuccessful login attempts.
- Monitoring and log for information disclosures that leave the information system.
System Assessment & Authorization
- Utilize interconnection security agreements and validate that appropriate controls are employed to determine the risk associated with connecting separate information systems
- Information system must be continuously monitored for threats and vulnerabilities.
Information System Backup
- Provide backup of user-level and system level information contained in the information system
- Provide alternate telecommunication services including necessary agreements to permit the resumption of NEXT-GEN SCOUT for essential mission and business functions
- Establish a “Safe Mode” when certain conditions such as reduced bandwidth or limited power. Restriction could include limiting only certain functions to operate.
Identification and Authentication
- The application shall use two-factor authentication to validate identity of the user
System and Communication Protections
- Ensure that the application protects against or limits the effects of denial service attacks.
- Ensure that priority protection is in place to prevent lower-priority processes from delaying or interfering with the information system servicing any higher-priority processes
- Information at rest shall be protected via encryption
System and Information Integrity
- The application should be able to detect extraneous content such as SQL injections. This would include the ability to perform information input validation checks.
- Malicious Code Protection mechanism at entry and exit points to detect and eradicate malicious code.
- The application must support tier 3 deployment
Federal Risk and Authorization Management Program (FedRAMP) Version 2.0
FedRAMP is a government-wide program that provides a standardized approach to security assessments, authorization, and continuous monitoring for cloud products and services. FedRAMP controls are based on NIST SP 800-53. FedRAMP authorized providers are available at https://marketplace.fedramp.gov/#!/products?sort=productName
- Cloud Service Offerings must be FedRAMP compliant
Additional Security References:
Privacy
California Privacy Policy and Privacy notice on collection requirements, (Government Code Section 11015.5 and 11019.9, and Civil Code Section 1798.17, when personal information is involved.
Accessibility
California Government Code section 7405 directs that: “state government entities, in developing, procuring, maintaining, or using electronic or IT, either indirectly or through the use of state funds by other entities, shall comply with the accessibility requirements of Section 508 of the Rehabilitation Act of 1973, as amended (29 U.S.C. Sec. 794d), and regulations implementing that act as set forth in Part 1194 of Title 36 of the Code of Federal Regulations.”
Government Code section 7405, in requiring compliance with Section 508, mandates that electronic and information technology (EIT) are accessible to individuals with disabilities, specifically:
State Agencies/state entities must develop, procure, maintain, or use EIT, that employees with disabilities have access to and use of information and data that is comparable to the access and use by employees who are not individuals with disabilities, unless an undue burden would be imposed on the Agency/state entity.
Individuals with disabilities, who are members of the public seeking information or services from an Agency/state entity, have access to and use of information and data that is comparable to that provided to the public who are not individuals with disabilities, unless an undue burden would be imposed on the Agency/state entity.